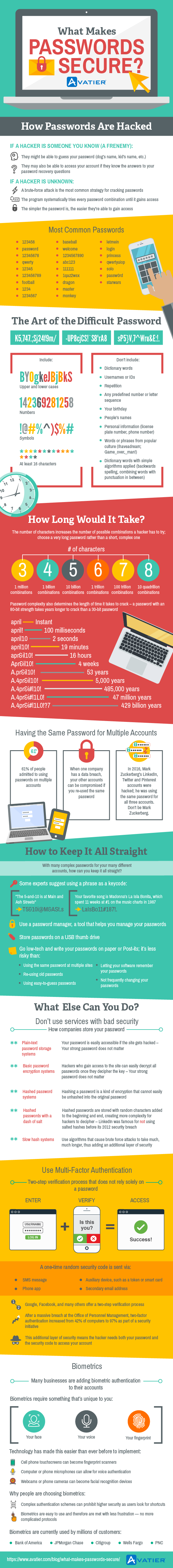
Passwords are hacked in a variety of ways and for a variety of reasons.
Sometimes the hacker is someone you know. It could be a “frenemy” who wants to access your information. If so, he or she might be able to guess your password if you use one that’s as obvious as your dog’s name or child’s name. Also, if you are not using a proven password management solution like Avatier, an insider may be able to access your account if the answers to your password recovery questions are known.
If a hacker is unknown to you, a brute force attack is the most common strategy for cracking your password. In this method, a program systematically tries every password combination until it gains access. That is why the simpler your password is, the easier it is for someone to gain access.
Paste this Image on Your Site!
Simply copy and paste the code below and you can share this infographic on your site:
The 25 most common passwords are:
- 123456
- password
- 12345678
- qwerty
- 12345
- 123456789
- football
- 1234
- 1234567
- baseball
- welcome
- 1234567890
- abc123
- 111111
- 1qaz2wsx
- dragon
- master
- monkey
- letmein
- login
- princess
- qwertyuiop
- solo
- passw0rd
- Starwars
The Art of the Difficult Password
A difficult password is your stronghold against hackers. Examples of high-security passwords include:
- K5,747.;Sj24f9m/
- -UP8cjCS!`S8″rA8
- sP5}V97^Wru&E:!
A difficult password is created by using variables, such as upper and lower cases, numbers, and symbols, along with a password length of at least 16 characters.
When creating your password, don’t include dictionary words, usernames or IDs, repetition, any predefined number or letter sequence, your birthday, people’s names, personal information (license plate number, phone number), words or phrases from popular culture (Ihaveadream; Game_over,_man!), or dictionary words with simple algorithms applied (backwards spelling, combining words with punctuation in between).
How Long Would It Take?
The number of characters in your password increases the number of possible combinations a hacker has to try. That is why it’s better to choose a very long password rather than a short, complex one.
- 3 characters: 1 million combinations
- 4 characters: 1 billion combinations
- 5 characters: 10 billion combinations
- 6 characters: 1 trillion combinations
- 7 characters: 100 trillion combinations
- 8 characters: 10 quadrillion combinations
Password complexity also determines the length of time it takes to crack. A password with an 80-bit strength takes years longer to crack than a 30-bit password.
Instantly cracked password: april
100 milliseconds: april!
2 seconds: april10
19 minutes: april10!
16 hours: apr&il10!
4 weeks: Apr&il10!
53 years: A.pr&il10!
5,000 years: A.4pr&il10!
485,000 years: A.4pr&i#l10!
47 million years: A.4pr&i#l1L0!
429 billion years: A.4pr&i#l1L0!?7
Also, it’s bad practice to have the same password for multiple accounts, even though 61% of people admit to doing it. We all know how inconvenient it is to have so many passwords, but when one company has a data breach, your other accounts can be compromised if you re-used the same password. In 2016, Mark Zuckerberg’s LinkedIn, Twitter, and Pinterest accounts were hacked; he was using the same password for all three accounts. Don’t be Mark Zuckerberg.
How to Keep It All Straight
With many complex passwords for your many different accounts, how can you keep it all straight? Some experts suggest using a phrase as a keycode. For example, the password “T5&10i@M&ASt.s” could be remembered using the keycode “The 5-and-10 is at Main and Ash Streets.” Similarly, the password “LaIsBo11#187!” could be remembered with this sentence about a favorite song: “Madonna’s La Isla Bonita, which spent 11 weeks at #1 on the music charts in 1987.”
Additionally, when we each have so many user accounts, password managers become useful tools to help keep your passwords straight. Another option is to store your passwords on a USB thumb drive.
Some even suggest you go low-tech and write your passwords on paper or Post-its. Surprisingly, it’s less risky than using the same password on multiple sites, re-using old passwords, using easy-to-guess passwords, letting your software remember your passwords, or not frequently changing your passwords.
What Else Can You Do?
A good rule of thumb is not to use services with bad security because the way that companies store your password will affect how easily you can be hacked. In plain-text password storage systems, your password is easily accessible if the site gets hacked. Your strong password does not matter. In basic password encryption systems, hackers who gain access to the site can easily decrypt all passwords once they decipher the key. Your strong password does not matter. In hashed password systems, hashing a password is a kind of encryption that cannot easily be unhashed into the original password. In hashed passwords with a dash of salt, the hashed passwords are stored with random characters added to the beginning and end, creating more complexity for hackers to decipher. LinkedIn was famous for not using salted hashes before its 2012 security breach. In slow hash systems, the algorithms that cause brute force attacks take much, much longer to crack the password, thus adding an additional layer of security.
Another way to add security to your login is to use multi-factor authentication. This is a two-step verification process that does not rely solely on a password, meaning the hacker needs both your password and the security code to access your account. A one-time random security code is sent via a SMS message, a phone app, an auxiliary device like a token or smart card, or a secondary email address. Services like Google, Facebook, and many others offer a two-step verification process. It has proved to be a valuable security protocol. After a massive breach at the Office of Personnel Management, two-factor authentication increased from 42% of computers to 97% as part of a security initiative.
Implementing biometric authentication is another way that businesses are amplifying their security practices. Rather than a security code being the second part of two-factor authentication, biometrics require something that’s unique to you, such as your face, your voice, or your fingerprint. Current technology has made this easier than ever before to implement. Cell phone touchscreens can become fingerprint scanners. Computer or phone microphones can allow for voice authentication. Webcams or phone cameras can become facial recognition devices.
People are choosing to implement biometric authentication because other, more complex authentication schemes may sometimes prohibit higher security as users look for shortcuts instead. Biometrics are easy to use and therefore are met with less frustration — no more complicated protocols. “As a security community, we’re finally realizing that having unusable security is akin to having no security at all,” said IEEE member Diogo Mónica.
Biometrics are currently used by millions of customers, including Bank of America, JPMorgan Chase, Citigroup, Wells Fargo, and PNC. “Fingerprint ID was the No. 1-requested feature from mobile users before we introduced it,” said a Bank of America spokesperson.
Did you know that Avatier Password Management now works directly in conjunction with RSA SecurID Management?
Sources:
https://www.cnet.com/how-to/the-guide-to-password-security-and-why-you-should-care/
http://www.telegraph.co.uk/technology/2016/01/26/most-common-passwords-revealed—and-theyre-ridiculously-easy-to/
http://passwordsgenerator.net/
http://lifehacker.com/5919918/how-your-passwords-are-stored-on-the-internet-and-when-your-password-strength-doesnt-matter
https://it.ucsf.edu/policies/bad-passwords
http://www.thegeekprofessor.com/guides/passwords/bad-passwords/
https://howsecureismypassword.net/
http://time.com/money/4358697/protect-passwords-after-zuckerberg-hack/
http://www.ctvnews.ca/sci-tech/hack-attacks-a-look-at-the-leaks-and-data-breaches-that-shook-the-world-in-2016-1.3203453
http://it.ucsf.edu/policies/how-choose-password
https://www.cnet.com/how-to/how-to-master-the-art-of-passwords/
http://lifehacker.com/5919918/how-your-passwords-are-stored-on-the-internet-and-when-your-password-strength-doesnt-matter
http://www.nextgov.com/cybersecurity/2015/08/4-charts-explain-state-agency-cybersecurity-after-opm-hack/118837/
http://www.cnbc.com/2016/04/05/biometrics-future-of-digital-cyber-security.html
https://www.nytimes.com/2016/06/22/business/dealbook/goodbye-password-banks-opt-to-scan-fingers-and-faces-instead.html
https://www.nerdwallet.com/blog/banking/biometrics-when-your-bank-scans-your-voice-face-or-eyes/